Zero Latency is one of our most important projects, if not the most important, aimed at achieving a differential position that will provide us with competitive advantages. With this project, we are going to increase our dependence on technologies, and with it we are also taking on greater risks in this area, since our business depends on the availability of these technologies to a greater extent. When we used to design our structures on drawing boards, our biggest problem could be fire. Now we have other hidden enemies within these technologies.
When the first viruses appeared, they were not designed to do harmful work. Their main goal was to be as visible as possible: in a similar way to today’s graffiti artists, they look for popularity. Those of you who are older still remember viruses like the “bouncing ball” virus. A ball would appear on your MSDOS screen, bouncing between your letters. It was annoying, but it didn’t go any further.
There were also the first “hackers”. People who connected to telephone exchanges to have “unlimited rates”, or others who wanted to see what was hidden behind computers without much intention of doing evil. I still remember that film, “WarGames”, in which the main character was looking for a game and almost ended up provoking a nuclear war.
From then until today, all this has evolved a lot.
These actors (called “Threat Actors”) have now become professionalised, and have turned into “Corporations” that only seek to maximise their profits.
And in this case, they do not care how much damage they may cause, if they can maximise their results. They come in two types, private criminal organisations – those that seek financial gain – and state-sponsored organisations that seek to attack critical infrastructure to undermine economies and geo-strategic targets.
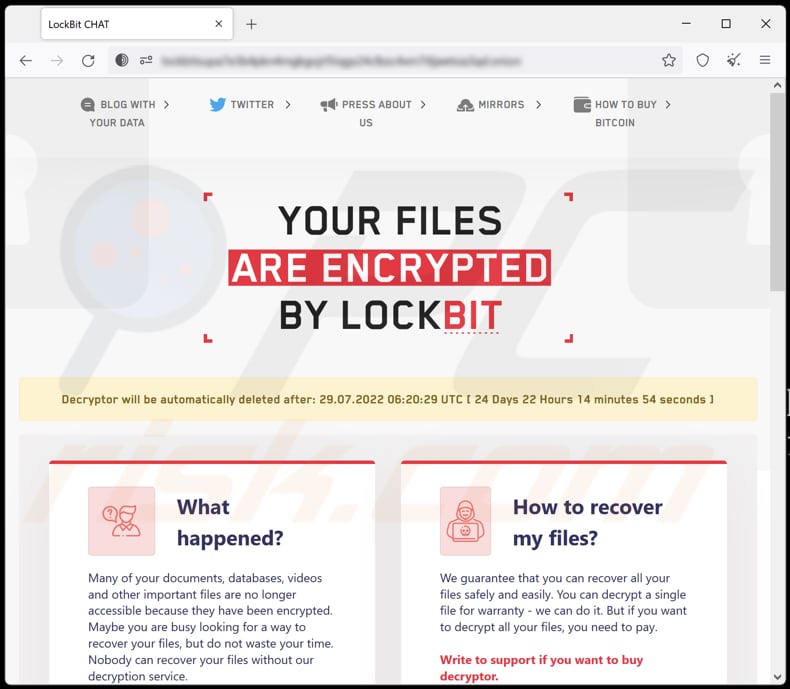
Now the leading private sector company of “Threat Actors” is currently LockBit. I am sure you have heard in the press about the fuel supply problems that occurred in May 2021 on the American East Coast (Colonial Pipeline), or the problems that occurred at the beginning of this year with the British postal service (Royal Mail) and the Hospital Clinic in Barcelona, among many others.
LockBit’s procedure is to copy the information and then leave it encrypted so that it cannot be accessed, so that they then ask for money, usually in cryptocurrencies, to be able to recover the information, and also for its “non-disclosure”, for not publishing it on the internet. As you know, the malicious software they use for this is called “Ransomware”. And if you do not know this, it is because you have not yet completed the “Security Training II”. Please ask your Human Resources department for it, as I think it is very important for all of you.
LockBit is considered a Ransomware-as-a-Service (RaaS) group, which means that it owns a ransomware variant, and sells access to it and its use to its affiliates, in exchange for a fixed fee, and a share of the profits made by the affiliate, who is actually the one carrying out the attack.
The price they ask for recovery and/or for non-disclosure and sale depends on who you are, what information they have taken, whether they think you are capable of recovering it without their help, and whether they consider you may be too sensitive to not publishing it.
They operate in a similar way to ordinary companies. They advertise, they put out job offers, they reward those who help them improve their software, … If you pay, they make sure you get your files back – they take care of their “credibility” – to the point that they have a support line to help you. If necessary they connect to your computers to recover your data themselves. If you don’t pay, they try to sell your data and publicise their sale to the world, so that everyone knows what happens to the non-payer.
A well-known victim was a children’s hospital in Canada (SickKids Hospital). The Lockbit organisation apologised after the attack, making every effort for a speedy recovery, and explaining that their affiliate had not followed their rules, their “code of ethics” with this attack.
´So why all this? Easy, we need your help´.
Imagine that I, an Aernnova user who only has access to the information I need to work with, (designs of a client, personal data of Aernnova employees, financial data or supplier data), have the misfortune of falling into their networks. Possibly my information will first be copied onto their servers and then encrypted to prevent us from accessing it. In the best scenario, the malware can be removed, the information can be recovered from a copy stored elsewhere, and nothing has been taken with sensitive non-public information. But what if they don’t? Surely you remember a case of a company in the sector that was down for more than a month with all its employees at home and production at a standstill. Without going into the reputational problems that this could have caused them and the consequences of the possible leakage of information with the possible corresponding financial claims.
We, your colleagues at CMIT, will try to make sure that your computers do not have security flaws, and we will put software in place that will try to stop malware in case it tries to run. We also make sure that files are only seen or accessed by those who need to access them, to avoid risks. We will make backups in case the worst happens, and we will make sure that no one from outside can access them. But this is a war between unequal actors: the “Malicious Actors” are many and well organised. It is estimated that, with the penultimate version of its Ransomware, LockBit made several hundred million dollars. Their financial incentive to attack us is very strong, and we have many points of entry to the safe, which is our data, our employees’ and our customers’ data.
And that is where you come in. It is in this defence that we want you. We need you to look at what link you click on, what programme you run, who you exchange information with. In the security training you have received (or will surely receive shortly) we have tried to give you a little guidance on what to look out for. But basically it is a bit of common sense. No one is giving us millions, or warning us that we are going to jail by email.
If you are not expecting the “package”, make sure it is for you before you click on it. Try to access it yourself by typing in your bank’s address and not by clicking on the link: I’m sure the bank has told you hundreds of times that they do not ask for passwords. If you don’t expect it, please hesitate. We have a lot at stake. We know this is starting to feel like paranoia, but please hesitate before clicking.
Thank you for your help.